1 "HOW SWEET TO BE A CLOUD FLOATING IN THE BLUE!""Due to decades of technology acquisitions to fuel growing businesses, enterprises are now facing a breaking point with their IT systems. Some systems can't share information and workloads, servers are highly underutilized and the cost of energy is becoming greater than the value of the systems the energy powers. In some cases, nearly 70 percent of companies' IT budgets can be devoted to managing, maintaining, securing and upgrading systems rather than building new capabilities, services and applications. Cloud computing changes these economics dramatically. An emerging compute model for delivering IT-related capabilities as a service, cloud computing promises dramatically better ease of use, economies of scale and much greater flexibility in sourcing and adapting to change. The technologies comprising cloud computing - virtualization, SOA, Software as a Service, request-driven provisioning - are technologies that IBM invented or is well-known for excelling in today. …. With today's announcements, IBM has the most complete set of hardware, software and services for enterprise clients to harness cloud computing for cost and efficiency benefits - while keeping their businesses secure, resilient and performing at optimal levels." - IBM Blue Cloud Initiative Advances Enterprise Cloud Computing I am writing this column just as we are finishing up with IBM Pulse, a conference focused on service management. Within this conference, we delivered a track on cloud computing for business leaders to discuss IBM's perspective on cloud computing and its supporting capabilities, technologies, and practices, along with adoption roadmaps for enterprises to derive business value. The track itself was divided into three major areas: the business imperative of cloud computing, the architecture, technologies and practices supporting cloud computing, and the approaches to ensure a successful implementation. The track ended with a panel session that fostered a conversation to address major concerns with cloud implementations, and a discussion on where cloud computing was headed in the near future. I will summarize the cloud computing track in this column as a way to start our discussion on the details through the rest of the year. 2 THE BUSINESS IMPERATIVE OF CLOUD COMPUTINGThe three sessions in this category focused on establishing why enterprises are embracing cloud computing and the value that they can derive from their investments. Companies are embracing change by innovating aggressively, mastering operational efficiency, and leveraging new business opportunities. The first session looked at cloud computing from a business perspective as providing a competitive edge. Companies can now respond faster to rapidly changing business conditions, drive the most value out of their existing systems and put existing and new processes in the direct control of the business - allowing them to achieve true alignment of business and IT. Cloud computing has continues to be one of the hottest IT topics for companies, and the deluge of information has led to a growing confusion. The second session served as a guide through cloud computing ensuring that the audience had a common understanding of the language, taxonomy, capabilities, technologies, and benefits. The session also provided IBM's unique perspective on cloud computing. The category ended with a look at the value that can be derived from cloud computing. Enterprises continue to have challenges in running and managing their business on IT infrastructures that have deployed increasingly disparate computing environments. One of the key drivers for cloud computing is the Return On Investment (ROI.) Cloud computing maximizes ROI through consolidation and virtualization of IT resources, increasing the efficiency of managing the resources, decreasing administrating costs, and increasing productivity. Through actual case studies, the session highlighted the benefits of cloud computing and the ROI.
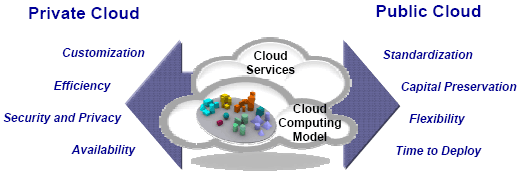
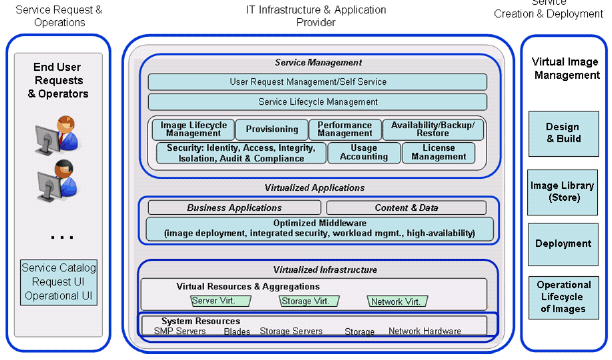
Figure 1: Cloud Computing Models As was pointed out in the introduction, businesses are challenged with an ever changing environment, economic chaos, and the need to reduce their operating costs to remain competitive. In addition, businesses are challenged with taking advantage of the new opportunities that are becoming available as our planet gets smarter through becoming more intelligent, more instrumented and more interconnected. These challenges are driving businesses towards an alignment of IT and business to ensure that changes can be handled with speed and agility. This alignment is accomplished through the establishment of a dynamic infrastructure that can deliver business services flexibly with speed and agility and help a business manage risk, reduce cost and improve service. Cloud computing provides the foundation and capabilities for the dynamic infrastructure through a consumption and delivery model for services in which the user sees only the service and has no need to know anything about the technology or implementation. The attributes provided by cloud computing - advanced virtualization of resources, rapid provisioning of these resources to application workloads, elastic scaling of these resources to address workload requirements, metering and billing of resources as they are used, delivery of the resources through flexible models (e.g. subscription, pay-as-you-go), the ability to order these services through catalogs, and the ability to consume the services through standardized web-based interfaces - provide the underlying capabilities to support the dynamic infrsatructure. Figure 1 shows the underlying cloud computing models. A private cloud owned and managed by the enterprise provides services with access limited to the enterprise and its partner network and drives efficiency, standardization and best practices while retaining greater customization and control. A public cloud is service provider owned and managed providing access to services by subscription. It delivers a select set of standardized business process, application and/or infrastructure services on a flexible price per use basis. Of course a federated service delivery model is feasible, allowing an enterprise to deliver its mission critical application services through its private cloud and using the public cloud for "spillover" requirements and to run its less mission critical workloads. Besides the cloud attributes (resource abstraction, rapid provisioning, elastic scaling, and flexible pricing) and the cloud delivery models (private, public, federated), the taxonomy of clouds includes the different participants involved in the cloud along with the attributes and technologies associated with addressing their needs and the different types of as-a-service offerings. The key roles in a cloud environment include the service consumer, the service creator and the service provider. The cloud service consumer needs a secure anytime anywhere access to low cost services that are flexible and easy to use. The biggest hurdle to adoption of cloud has to do with consumers discomfort in the following areas: security of both service and the underlying data, service availability and reliability, service management to ensure service level agreements, ensuring control over access and policies, and the appropriate administration to facilitate flexible pricing structures. A service does not exist unless someone actually creates it. The cloud services creator needs tools and capabilities to offer differentiated services, offer incentives to ensure that consumers keep coming back to use the services, and the ability to change services on-demand to stay competitive and address threats. Finally the service provider actually runs the service that the service consumer wants and was designed and developed by the service creator. The service provider needs their IT resources integrated so their usage is optimized, the ability to add/remove resources on demand, a non-disruptive way to save money, and the means to charge for usage. There are three basic categories of cloud services: infrastructure services which provides access to a virtualized pool of resources, platform services that provide middleware or an application stack (hardware, operating system, software), and application services that provide access to a specific application or business process (e.g. HR services, email services, collaboration service.) Where these services are deployed defines the type of cloud service. Private cloud services are hosted within the intranet while cloud services deployed in the internet are called public cloud services. It is critical to understand the workload characteristics to identify deployment strategies for a specific service. Determining the value that can be delivered by cloud computing requires an analysis similar to other Return On Investment (ROI) analysis. The first step is to determine the Key Performance Indicators (KPIs) that will be used as the metrics for the value analysis. The second step is to gather the data for these metrics in the as-is environment and to-be environment to show the potential improvements. Also in this step the one-time implementation costs are determined. Finally, the analysis is done on the data gathered to determine the overall ROI and associated characteristics (e.g. payback period.) There are many exciting showcases of the value delivered from cloud computing, including IBM's own Technology Adoption Program (TAP) for managing technology to drive innovation for internal transformation and growth. The goal of the program is to enable 2,500 IBM innovators to quickly and easily prototype and deploy new technologies for 125,000 early adopters who will use and provide feedback on the new applications. Through cloud computing, TAP was able to realize annual savings of over $3M with a payback period of a mere 73 days and an ROI of over 1000%. 3 CLOUD COMPUTING ARCHITECTURE, TECHNOLOGIES AND PRACTICESThe five sessions in this category focused on detailing the architectural model for cloud computing, the management aspects of a cloud computing environment, the capabilities required to support a cloud, the key technologies provided by IBM to support cloud computing, and a deep dive into cloud security issues. Delivering effective cloud services requires a new service delivery approach. The first session reviewed IBM's architectural approach to building a cloud service delivery platform model and walked through several client scenarios to show the underlying capabilities and technologies. The architectural model was followed by a session that examined the service management challenges presented by cloud computing and explored how IBM capabilities address these challenges. Cloud computing provides services that are easily configured, deployed, dynamically-scaled, and managed in virtualized environments. These cloud services must be tied into business processes, data models, security services and the enterprises' service management, problem resolution, and compliance processes. Following this architecture focus, the next two sessions focused on the capabilities and technologies supporting cloud computing. Enterprises will enter into cloud computing driven by their business objectives and needs. Addressing these business entry points into Cloud Computing requires appropriate capabilities and technologies along with the know-how of designing, implementing and deploying solutions. The next session discussed the IBM Cloud Computing portfolio, and how the underlying capabilities, technologies, and services can support an enterprises' cloud computing implementation. This was followed by a session that focused on IBM's new Service Management Center for Cloud Computing which provides a comprehensive set of capabilities to support an enterprises' cloud computing implementation. This session explores the capabilities within the Service Management Center for cloud computing in the context of business scenarios and reviewed the early experiences through client case studies. This category of sessions ended with a focus on security concerns and the underlying practices. Security is considered one of the major barriers for the adoption of Cloud Computing. Enterprises are concerned with trusting an entity outside their enterprises' boundaries with their data along with the other related issues of ensuring privacy, having appropriate control, and the ability to comply with regulations. This session explored these security issues in the context of the cloud, described the comprehensive capabilities needed to manage risk and compliance, and walked through IBM's Security Framework to show how it addresses these issues. The architectural model shown in Figure 2 shows the comprehensive set of capabilities required to address the needs of the major roles in a cloud environment - the consumer of the cloud service, the provider of the cloud service, and the creator of the crowd service. The cloud service creator component has capabilities targeting all aspects of the lifecycle of the "image" that is used to bundle the service that is accessible by the consumer. This "image" can include the IT resources (e.g. server, storage, network), the operating system, the middleware, and the applications. The capabilities support the need to design and build the image, store it in the library of images that can be accessed by the users, the deployment of the images, and the management of the images through the entire operational lifecycle. The cloud service consumer serves both the end users and the operators that manage the infrastructure. The capabilities in this component ensure that the images that can be accessed are defined in a catalog, and have appropriate role-based user interfaces to access and manipulate the images. The key capabilities of the reference architecture are defined in the service provider component. The lowest layer of the architecture defines the capabilities of the virtualized infrastructure. These capabilities facilitates virtualization of all IT resources: server, storage and network. These virtualization capabilities can handle all types of IT resources, e.g. both mainframe and distributed servers. The next layer provides an optimized middleware with capabilities for image deployment, integrated security, workload management, and high-availability. The optimized middleware is used as the way to deliver services and information built according to well defined SOA and Information architectures. The central piece of the component is service management which provides the capabilities to manage a cloud service. These services include capabilities to handle user requests: managing the self service requests made by users, the lifecyle of images, and the provisioning of images based on the request. The capabilities also handle many of the qualities of service associated with delivering images, including availability, backup and restore, security and compliance, and performance management. To facilitate delivery through flexible models, the capabilities also support usage accounting and license management.
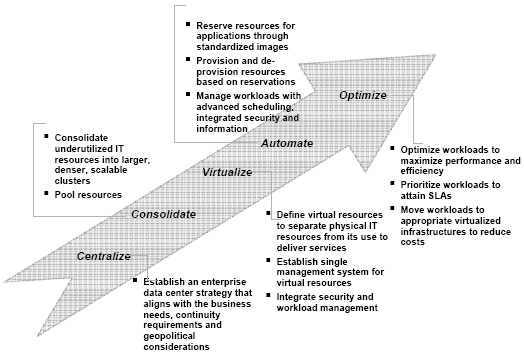
Figure 2: Cloud Computing Architectural Model The reference architecture provides a comprehensive set of capabilities to ensure that cloud services can be built, deployed, accessed, delivered and managed. Each of these capabilities are supported by the appropriate standards, technologies and tools - all integrated to work together to deliver cloud computing. As shown in the figure, many of the components need management - from the virtualized resources through the workloads and into the images, usage and service requests. The virtualized resource management focuses on deploying cloud services on virtualized resources and managing cloud services, images, and resources. The workload scheduling and management focuses on defining workloads along with Qualities of Service (QoS) requirements, assigning resources to workloads, adding/removing resources based on workload needs, and monitoring workloads. Image lifecycle management which focuses on designing and building images for cloud services, and managing images through their lifecycle. Service automation management which streamlines and automates management of cloud services and addresses all aspects of the cloud service lifecycle. Finally, usage and accounting management which helps define business and IT metrics, meter usage of services and resources, and accounting based on delivery model, e.g. subscription, pay-as-you-go, etc. IBM provides a comprehensive portfolio of services, products, technologies and experiences to enable enterprises to leverage cloud computing to address their needs. The services portfolio provides consulting on establishing a strategy and approach for an enterprises' cloud journey, to implementation services to ensure successful deployment of clouds, to specific managed cloud services that enterprises' can use directly and flexibly based on their requirements. The products and technologies portfolio provides hardware and software to address all the needs that an enterprise would need to leverage cloud computing. The hardware technologies focus on resource virtualization and management while the software technologies focus on service management. IBM Tivoli Service Management Center for Cloud Computing provides a comprehensive service management solution to simplify customers' cloud journey to deliver cloud services with speed, flexibility, scale, and security. The capabilities provided can be used by enterprises to address their specific needs. For example, Tivoli Provisioning Manager 7.1 provides support for deploying virtual machines, storage and networks in the enterprises' dynamic infrastructure. To address data protection and recovery concerns, IBM Managed Data Protection supports desktop and laptop data protection with Tivoli Continuous Data Protection. An integrated cloud service management environment is provided by Tivoli Service Automation Manager 7.1 which includes service-consumer interfaces, additional workflows, content and application integration to facilitate delivery of infrastructure and platform as-a-service. Many surveys show that security is usually the main concern for any new IT solution, but the additional "external" aspects of the cloud exacerbate this concern. Enterprises are mostly concerned about the data security and the reliability of cloud computing in practice. Currently, large enterprises have a bias towards private clouds which was considered to be more secure than any external solutions. IBM has defined a security framework as the basis for building a comprehensive portfolio of technologies and services to address cloud security. For security considerations at the physical resource and infrastructure levels, the security framework addresses issues on data location, disaster recover, virtualization security and enterprise security. For application and process, the framework supports compliance and auditing technologies along with support for investigating the audit trails and logs. For data security, the framework supports data segregation and recover technologies. Finally, for people and identity security, the framework supports identity federation amond cloud services as well as privileged access control. This support is provided through both technologies that can be integrated by the enterprise in their cloud implementations as well as through managed services that can be used by the enterprise as needed. 4 SUCCESSFUL CLOUD IMPLEMENTATIONThe four sessions in the final category focused on how enterprises can successfully implement clouds. Each enterprise will adopt Client computing differently based on their objectives, their current environment and capabilities, and the business value that they want to derive. The first session in this category explored the roadmap to transform an enterprise data center by adopting cloud computing based on building capabilities from their current as-is state to their desired to-be state. The session also explored migration options and when it makes sense to adopt certain technologies. The next session distilled the unique characteristics of clouds and described how to best think about deployments in the clouds. This session included the lessons learned from the cloud projects that we have conducted with our customers (and internally) and highlighted early patterns and anti-patterns that we are uncovering. To take full advantage of Cloud Computing requires a re-engineering of the business applications and corresponding legacy IT systems that support it. The next session in this category looked at all aspects of the modernization effort including how to understand and harness the complexities inherent in business applications, how to use agile re-engineering methods, how to align IT systems with business, and how to "eat the IT elephant one bite at a time." The track ended with a panel that discussed the main issues that can hamper an enterprises' adoption of cloud computing: changing the organizational behavior, effective governance of (cloud) services, and adoption of standards to facilitate use of cloud services. This interactive session allowed participants to get their concerns addressed, and provided insights from early experiences. This category of sessions started with a look at the enterprises cloud journey. The adoption path is depicted in Figure 3 which shows a progression starting with centralize which focuses on reducing the number of data centers and infrastructure complexity, to consolidate which reduces redundancy and wastage of IT resources along with the space needed for the IT resources, to virtualize which separates the application workloads from the infrastructure and manages the virtualized environment, to automate which removes the manual processes of running the business by automating provisioning and through usage and metering services of the resources, and finally to optimize where the system can sense and respond to changing workload requirements and move these workloads to best-fit infrastructures. The figure also shows the typical projects that are initiated in each of the adoption phases. Based on our experiences to date, we have identified three major business scenarios. In the automated provisioning scenario, businesses are challenged with time to market of business growth initiatives impacted by deployment capability of IT resources, high labor costs associated with manual IT resource deployment processes and procedures, excessive infrastructure costs associated with underutilized IT resources, compliance and audit posture impacted by human error during IT resource deployments, and the inability to respond to variations and spikes in demand. The solution to address these challenges include self-service provisioning of virtualized IT resources, user initiated scheduling and reservation through service catalog model of IT resources, self-service provisioning of pre-configured application / middleware stacks, customized deployment workflows implementing customer specific processes and enforcing customer specific policies, and an integrated service management of the provisioning environment.
Figure 3: Cloud Computing Adoption Progression The workload management scenario addresses the challenges of business agility being limited due to workloads being tied to IT resources, the inability to migrate workloads to more cost effective and efficient compute environments, the inability to respond to variations and spikes in demand, and the time to market of business growth initiatives impacted by availability of compatible IT resources to handle new workloads. The solution to address these challenges include an integrated modeling environment for infrastructure resources aligned to workload requirements, a user interface with support for administrators to deploy workloads to cloud environments, process-driven workflows to orchestrate deployment hand-offs, and spill-over to hosted external cloud environment for peak capacity periods. The service delivery platform scenario addresses the challenges of growing the customer base for existing service offerings, faster time-to-market of new service offerings, reducing on-boarding time for new customers, quickly responding to changes in market demand, flexible billing models for service offerings, and delivering services with shared infrastructure and cost effective security model. The solution addresses these challenges by self-service request and subscription model for end users, deployment of new service requests based on current resource allocation and utilization, usage metering of services and supporting resources warehoused to enable variable billing models, a comprehensive security framework, and a service bus model for mediation of end user service requests between internal and external providers. IBM has also expanded its support for modernizing heritage and legacy applications to allow them to leverage clouds. The modernization approach includes making heritage and legacy applications available as services in a service oriented architecture, providing RESTful interfaces to make them easily accessible through the web, and making them deployable on cloud based infrastructures. The portfolio of services and technologies supports this modernization through the entire lifecycle: strategy, design, modeling, assembly, testing, deployment and management. The final Panel session discussed the many issues that enterprises continue to be concerned about as they progress through their cloud journey, primarily around the intertwined issues of governance, security and standards. It is well documented that the most difficult aspects of any transformation concern an organization and cultural change along with the changing roles and responsibilities of the people. Governance is critical in ensuring a successful transformation as it provides a decision rights framework along with the policies to control the decisions and the ability to measure the effectiveness. We have already discussed the issues of security. Standards play an important role to ensure interoperability, integration and portability within the enterprise and across other service providers. These issues are intertwined as governance is needed to mitigate risk and compliance issues and requires standards to be effective in a cloud environment. Security is a critical component in setting up governance roles, responsibilities and decision making rights, and require standards to be addressed effectively across all layers of the cloud environment. In summary, Pulse provided an end-to-end insight into the value, issues, capabilities, and experiences into cloud computing. This lays the foundation for our detailed look at several areas as we take a deeper dive into the clouds through the next few articles. So, hop on the plane, fasten your seatbelts, and enjoy the rest of our journey through the clouds!About the author
Mahesh Dodani: "The Silver Lining of Cloud Computing", in Journal of Object Technology, vol. 8, no. 2, March-April 2009, pages 29-38 http://www.jot.fm/issues/issue_2009_03/column3/ |
|||||